
IT security plan
Phishing, ransomware attacks, zero-day exploits – the methods used by cyber-attackers are not only becoming more varied, but increasingly sophisticated too. And if data end up in the wrong hands, the consequences for companies in particular can be devastating. That is why it’s even more important to protect yourself against cyber-attacks in advance. We can help you do that, by providing a comprehensive IT security solution.
Focus on small and medium-sized enterprises
IT security: For SMEs, it’s more important than ever
“For SMEs, the risk of being affected by a cyber-incident is considerably greater than for large companies,” said the German Federal Office for Information Security (BSI) in its latest brochure “Cybersicherheit für KMU” (Cybersecurity for SMEs) (Version date: 26 July 2024). The reason? Outdated IT infrastructures combined with insufficient security measures, if any. As hackers get smarter and even automate their attacks, these kinds of security gaps present a very high risk. The attacks themselves are rarely targeted at small and medium-sized enterprises (SMEs). But these businesses will find themselves in a particularly unfortunate position if their infrastructure ever needs to withstand a widely dispersed attack.
The good news is that cybersecurity is not a battle you need to fight on your own. As an established provider of IT services, we will help you set up or reorganize your infrastructure to ensure IT security.
Procedure
An IT security plan from GOB: how we work
Not only the IT infrastructure will vary significantly, depending on the company or organisation. The work processes too will be put together differently and will require specific measures. The demands placed on your infrastructure will significantly depend on factors such as home-based working arrangements, cooperation with external partners and many other aspects besides. An IT security plan from GOB focuses on you and the specific needs of your company or organisation. When drawing up the plan, we will investigate all relevant aspects and will work with you to draw up the most effective possible plan that fulfils your needs.
IT security: 6 categories you ought to know
Your IT security plan is based on an analysis of six key areas you should pay attention to if you wish to ensure comprehensive protection against hacker attacks:
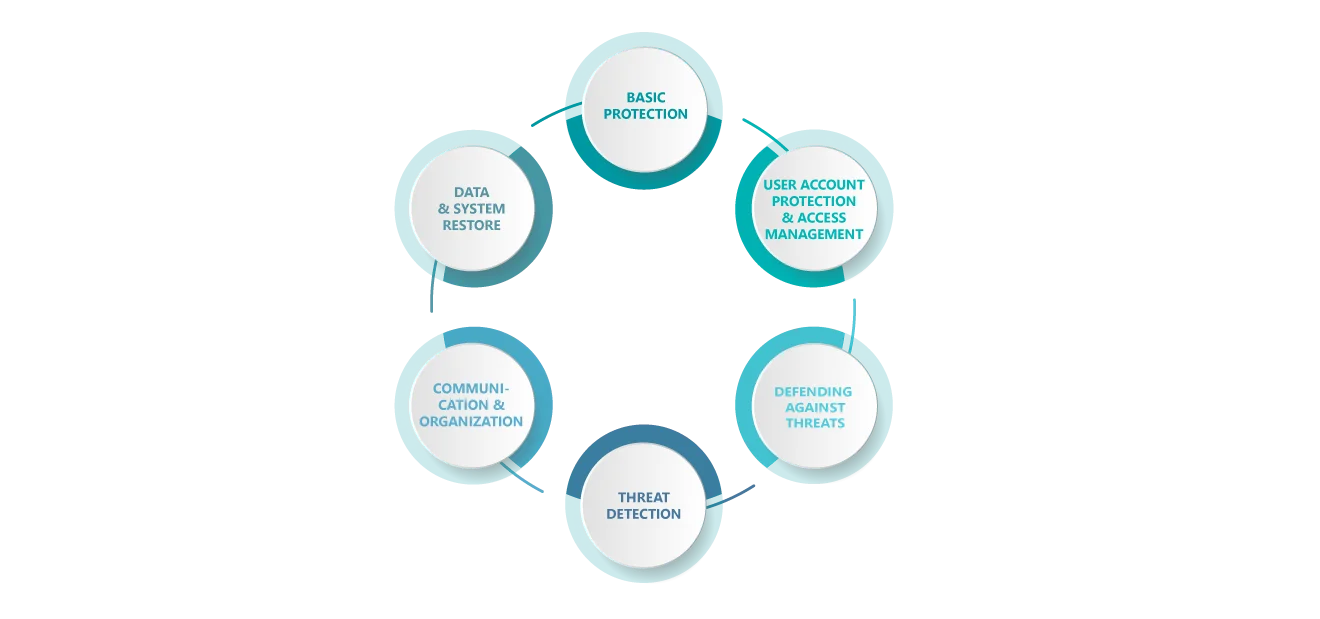
6 categories for your security
How secure is your infrastructure?
Depending on the infrastructure and the use case, different measures can be determined for the relevant areas. By working with you, we will draw up a plan that is tailored to the processes and measures that are relevant to you.
Below, you can find more in-depth information about the individual areas, together with some typical measures that you can take to boost the protection of your infrastructure.
Basic protection is a pre-requisite for all other IT security measures. If your IT infrastructure is based on outdated technologies and/or lacks underlying protection mechanisms, it will become an easy target for hackers. As technologies develop, the basic protection you have put in place needs to be evaluated at regular intervals and adapted if necessary. Only that way can you make sure you are one step ahead of potential attackers.
Nowadays, secure basic protection is nowhere near enough. For hackers, user accounts are also a popular point of entry that allows them to sneak into companies’ systems. By putting in place adequate user account protection, you will reduce the opportunities to stage an attack. An access management system is also an indispensable addition to any correctly set up account protection system. If a user account is compromised, the access management system will help minimize the damage by preventing harmful software from spreading.
Defending against threats is also an essential component of GOB’s IT security plan and is included under the heading of Prevention measures. Patterns of attacks are recognised and defined, so that attacks can be detected in advance and suitable action taken, before the attacks are even carried out.
Should preventative measures fail and if an attack occurs despite all of the care that has been taken, observing the ongoing threat in real time is indispensable. Threat detection therefore also forms an essential part of a comprehensive security plan. Any anomalies in the system will be reported without delay, before any damage has been caused.
IT security not only depends on technological measures. The concept of humans as the weakest link still represents a very high risk for companies and organisations. So it is even more important not to neglect communication and organisation. By training employees, introducing codes of conduct and drawing up and communicating an emergency plan to be used in worst-case scenarios, you can shape and design your company’s defence against cyber-attacks many times more efficiently.
Picture this: Your infrastructure falls victim to a ransomware attack and all of your data are suddenly encrypted and no longer accessible. So you decide to make use of your back-up to launch a system restore, but then realise that your back-up has also fallen victim to the ransomware attack and it too is no longer accessible!
And even though your infrastructure is set up in the best possible way, fully protecting it against hacker attacks simply isn’t possible. That’s why it is even more important to protect the data and system restore separately as part of a carefully considered security plan, in order to be certain that resilient back-ups are always available. Only that way can you ensure that in a worst-case scenario, you can restore your data, instead of losing them entirely.
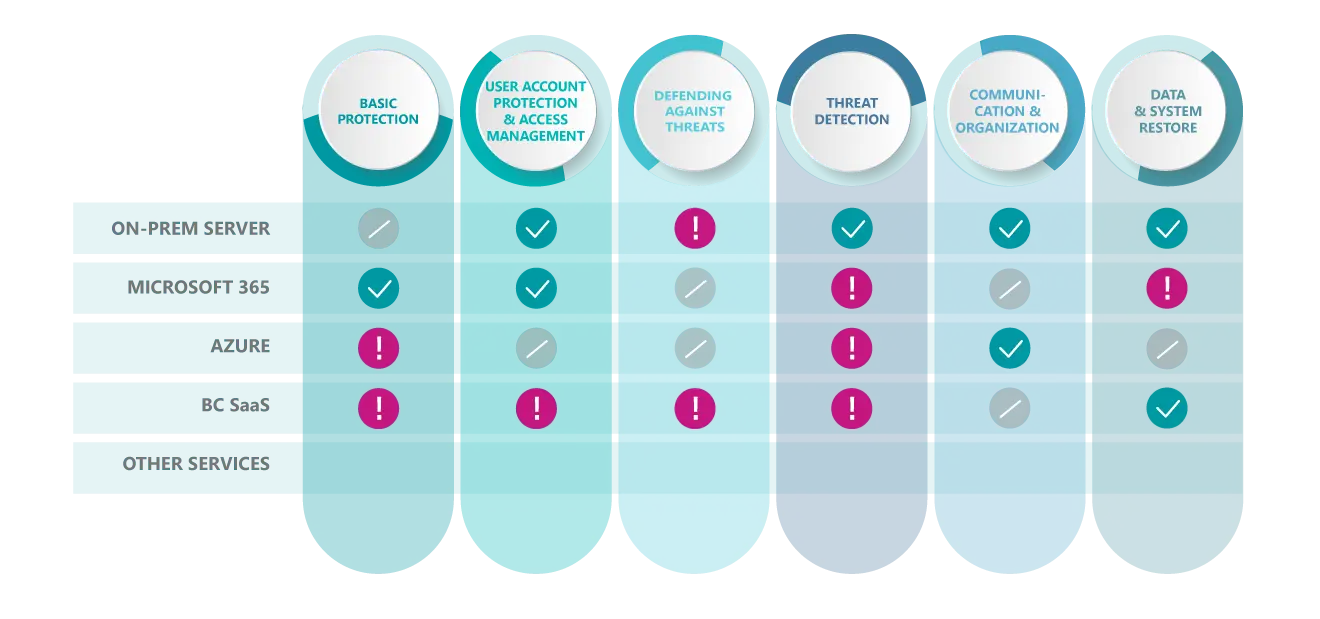
Security check
The reality: Are there any potential security gaps?
Based on the six categories mentioned above, we will carry out a thorough examination of your IT landscape. We will analyse the various components (such as on-prem servers, cloud services and so on) to identify any potential security gaps affecting any part of your IT infrastructure. We will then provide you with our recommendations for a basic level of security, sorted according to urgency.
Innovating. Transforming. Securing.
The GOB IT security plan
Trust is good, but verification is better – especially where your company’s IT infrastructure is concerned. A solid IT security plan takes into account all relevant components of the infrastructure concerned and is based upon the zero-trust principle. What this involves is explained below.
Definition
The zero-trust principle – explained simply
In a nutshell, the zero-trust principle means no-one is trusted by default. In other words, if the zero-trust principle predominates in a communication environment, the participants must first of all prove their identity, before they can enter the protected system.
The assignment of rights is therefore considerably more restricted than in conventional environments. It is based on a very extensive examination of the instances involved. With this in mind, stringent access guidelines (known as “conditional access policies”) are in force to guarantee that the IT infrastructure is fully protected.
Under the zero-trust principle, however, the trust that is granted lasts only for a short period. For each action, strong authentication will once again be required. The assignment of rights is also subject to some strict criteria:
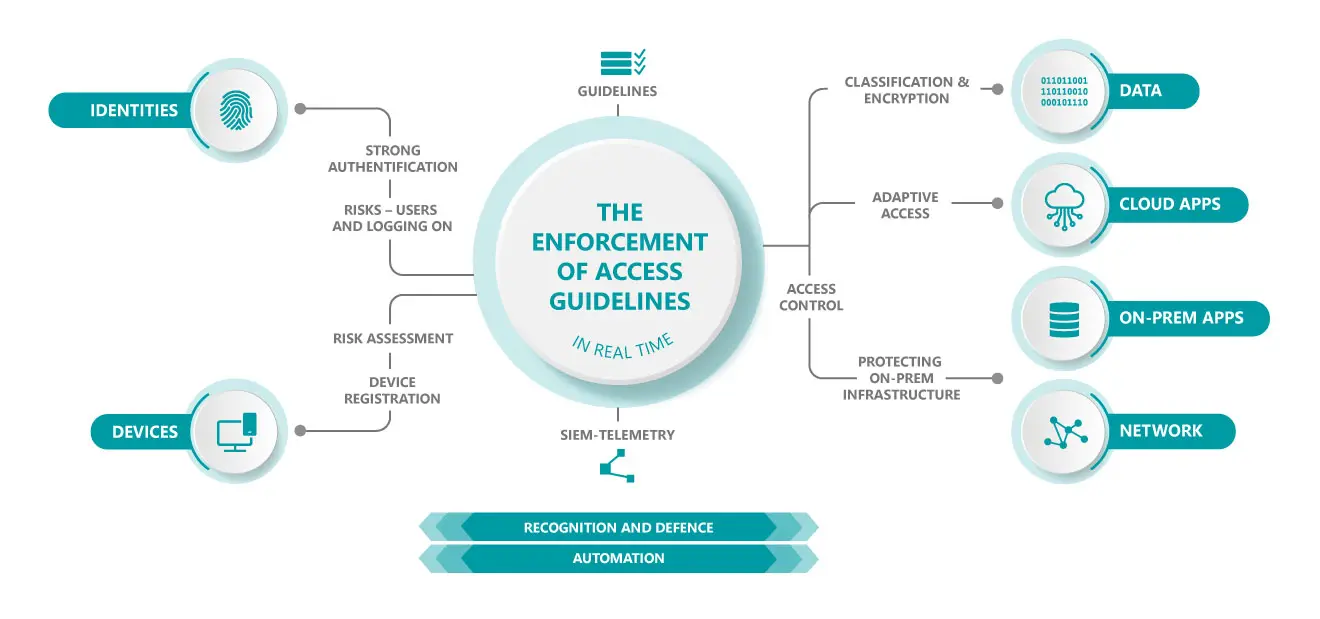
In a nutshell
The GOB IT zero-trust security plan
Using our zero-trust security plan, we can help you protect your company’s data against unauthorized access.
This means you can ensure that the information circulating within your network doesn’t end up in the wrong hands, and can prevent the data from being compromised.
Beside is a list of measures we frequently use as part of our security plan. This list is intended to illustrate the current methods of enhancing your protection, but must not be regarded as exhaustive.
A zero-trust concept goes hand in hand with strong authentication methods capable of verifying identities reliably. By implementing a central access system, you will be on the safe side: Your employees can log on via a single secure location, for which you can define very high security standards.
Registering devices permitted to access your system is another important component of a comprehensive security plan. This guarantees that only authorized end-user devices are able to access your infrastructure.
Access guidelines define how you assign rights and form the basis for the subsequent access control. They protect all of your company’s resources against unauthorized access. Depending on the infrastructure, rights can be assigned in a very nuanced way. Whether we are talking about cloud, on-prem, a network or data – access is allowed, subjected to certain restrictions or refused entirely, depending on the identities and devices concerned.
SIEM telemetry enables you to recognize potential threats before they penetrate the system and/or cause any harm. SIEM stands for Security Information and Event Management. SIEM telemetry analyses all log files in real time, always keeps an eye on your systems and immediately reports any anomalies. Assessment is carried out fully automatically and based on a continuous analysis of all instances involved (identities, devices, access guidelines, etc.).
Making technologies usable. But secure!
A comprehensive IT security plan: We’ll be pleased to advise you.
Want to receive professional advice about drawing up a tailored security plan? From risk analysis to implementation, we can help you to identify any gaps in your security and will then work with you to draw up a comprehensive IT security plan to protect your company or organization. In addition to advising you and drawing up the most effective plan, we can also provide you with targeted training to increase awareness amongst your employees.
Do you have any questions on the subject of IT security or want to find out more about the types of measures that can be taken? We look forward to hearing from you!